SECURE SOCKETS LAYER LEARNING [COMPLETE]
Using only a simple packet sniffer, an attacker can easily intercept data being sent accross the Internet, or even a LAN. As a result, data sent in plain text will surely not remain safe.
Therein lies the need for encryption standards, which allow passage of data from one system to another.
SSL INTRODUCTION
Secure Socket Layer was developed by Netscape, with its main aim to create a secure protocol to ensure that a client and host could communicate or transfer data and information securely.
SSL is what makes secure e-commerce and e-banking possible.
It is important to note that SSL has been succeeded by Transport Layer Security(TLS)
which is quite similar in its working and concepts to its predecessor.
SSL FUNCTIONS
SSL encrypts data at the sender's end and decrypts data at the reciever's end.
Such encryption and decryption of data also ensure that an attacker cannot intercept the data in transit, tamper with it , or even execute Man-In-the-Middle impersonation attacks.
Any tampering done with SSL encrypted data is usually easily detected through built-in checksum tests.
SSL provides for two-way authentication -that is both client's and server's identity are verified.
Another reason behind the widespread use of SSL protocol is that it is application protocol independent and can be used with absolutely any high level protocol.
SSL FEATURES
SSL-encrypted connection : This provides for the secure transaction of encrypted data between the client and the host. This feature of SSL performs the encryption and decryption of the data packets being sent between the client and server.
SSL client authentication : This optional feature allows for verification of the client's identity and prevents identity hijacks, or spoofing attacks. Hence this feature makes it difficult for a malicious attacker to fool the destination system into believing that the attacker system is the client.
SSL server authentication : This allows for verification of server's Certificate Authority (CA), which is the certificate given to the server by companies such as Verisign, Cybertrust,Thwate and others. This SSL feature is a very good countermeasure against phishing attacks.
SSL PROTOCOL COMPONENT
The main SSL protocol is made up of the following two sub-protocols:
SSL Record Protocol : This protocol looks after the transmission of the encrypted data and the format in which it is being transmitted. In addition, it ensures data integrity in the transfer process and also ensures that no data is lost in the transit from the source to destination.
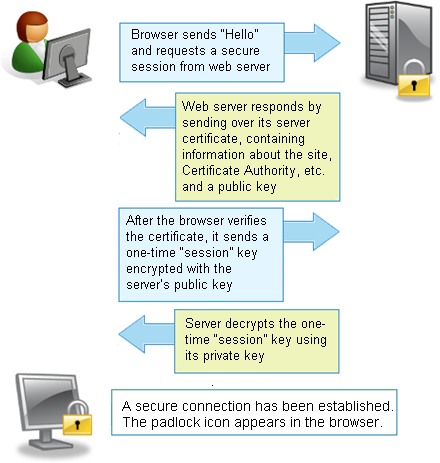
SSL Handshake Protocol: This protocol helps to determine the session key, which is the secret symmetrical key used to encrypt data after a SSL connection has been established between client and the host. Without this protocol, secure communication would not be possible.
DETERMINING WHETHER YOUR CONNECTION IS SECURE
There are several ways to determine whether your connection is safe :
Check your browser's status bar : This is the easiest ways to determine whether your connection is secure. If you see a closed padlock , then the connection is secure, else if the padlock is open or is not visible, the connection with remote server is not secure.
Check your browser's URL box: If the connection is secure , you will see https:// , else you will as http:// in the URL box.
Check for Certificate Authority : To determine whether the page you have visited has a CA, click on URL box as shown in image. Look for the Connection field. This field should normally display the Web site's Certificate Authority. It is important to note that sometimes malicious Web designers can forge a certificate or display a fake one.
A typical SSL transaction involves various encryption algorithms such as RSA, DSS, DES,RC4. It is within these encryption algorithms where the vulnerability of SSL lies.Over the years, it has been proven that SSL is not secure as it seems to be. The problem lies int the fact that the encryption algorithm used along with SSL are not foolproof and can easily be cracked using bruteforce techniques running on a powerful computer. Using this technique , all SSL versions below 3.0 (SSL 1.0 , SSL 2.0) have already been cracked.
However SSL 3.0 with 128 bits, will take a very long time.
168-bit encryption is also available. Note, however that higher encryption levels are not allowed for use outside the US due to national security reasons
That' all much about SSL ,still its a vast topic overall....Hope you understood pretty well about SSL stuff.
If you have any doubts, feel free to comment below





0 Comments
Post a Comment